100 Days of Cloud (Azure Edition)
Day 15 of Cloud (Azure Edition)
AZURE
Nyan
12/8/2025
Day 15: Create and Configure Network Security Group (NSG) in Azure
Task: The Nautilus DevOps team is strategizing the migration of a portion of their infrastructure to the Azure cloud. Recognizing the scale of this undertaking, they have opted to approach the migration in incremental steps rather than as a single massive transition. To achieve this, they have segmented large tasks into smaller, more manageable units. This granular approach enables the team to execute the migration in gradual phases, ensuring smoother implementation and minimizing disruption to ongoing operations. By breaking down the migration into smaller tasks, the Nautilus DevOps team can systematically progress through each stage, allowing for better control, risk mitigation, and optimization of resources throughout the migration process.
For this task, create a network security group (NSG) with the following requirements:
Name of the NSG should be datacenter-nsg.
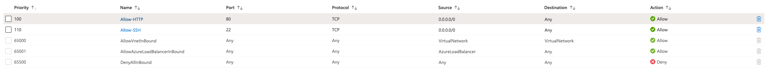
Add an inbound security rule named Allow-HTTP for HTTP service on port 80, with the source CIDR range of 0.0.0.0/0.
Add another inbound security rule named Allow-SSH for SSH service on port 22, with the source CIDR range of 0.0.0.0/0.
Use below given Azure Credentials: (You can run the `showcreds` command on the `azure-client` host to retrieve these credentials)
Day 15 of 100 Days of Cloud (Azure Edition) : Solution
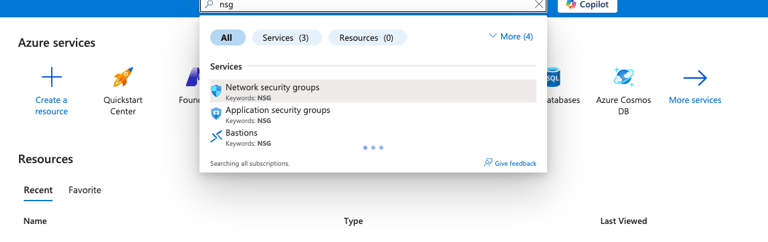
Type NSG in the search box and choose Network Security Groups.
Day 15 of 100 Days of Cloud (Azure Edition) : Cheers


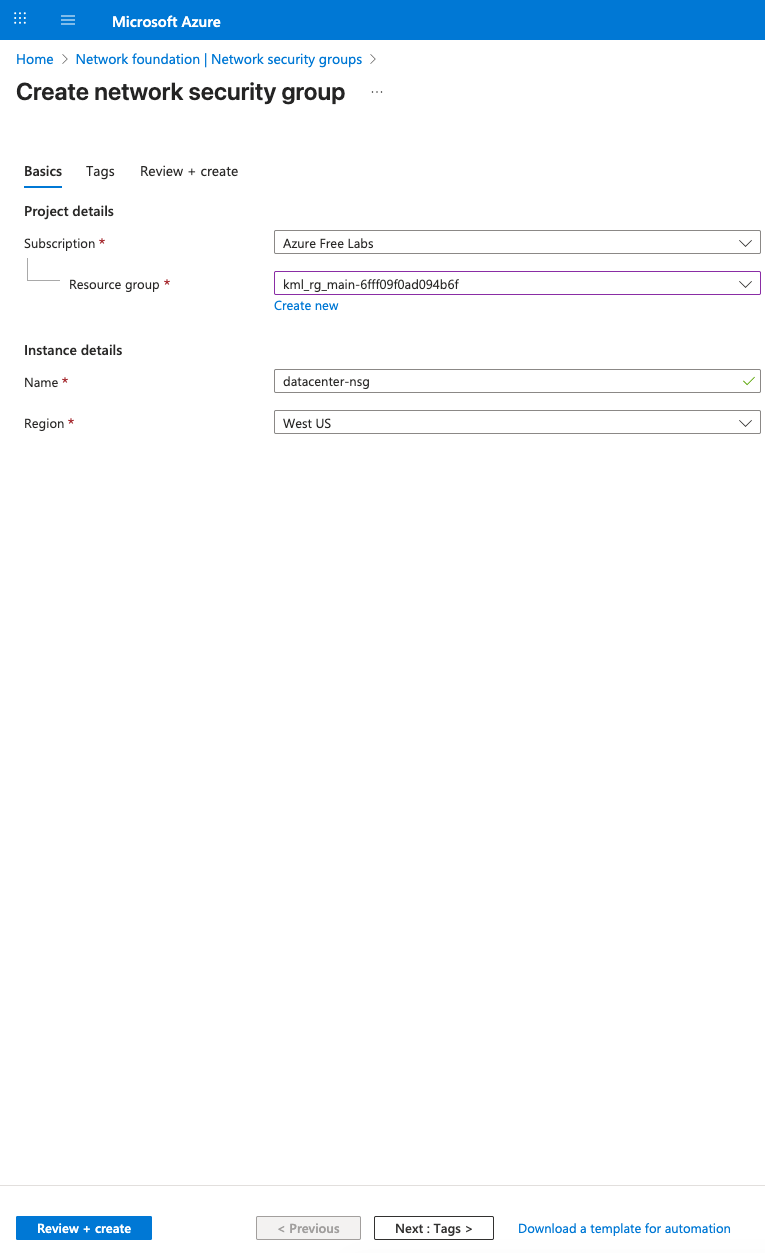

Choose the existing resource group and name as datacenter-nsg.
Click Review + Create button.
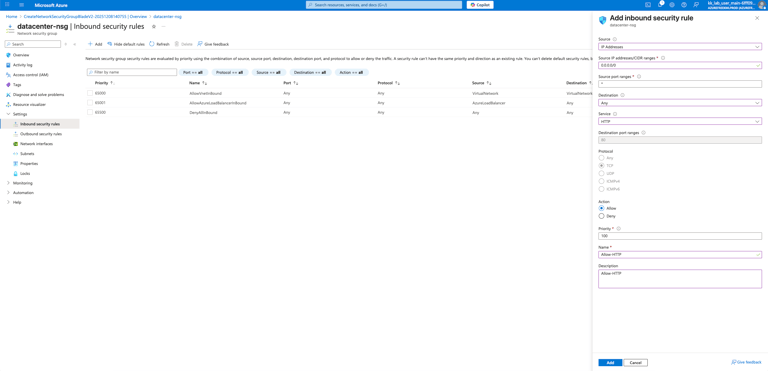
Choose Inbound security rules.
Click Add button.
In Source, choose IP Addresses and In Source IP addresses/ CIDR ranges, set 0.0.0.0/0 and In Source port ranges, set *.
For the Destination, set Any and choose Service as HTTP, destination port ranges will be automatically 80, and protocol as TCP.
Choose action as Allow.
Choose Priority as 100.
Name as Allow-HTTP.
Description as you prefer.

Choose Inbound security rules.
Click Add button.
In Source, choose IP Addresses and In Source IP addresses/ CIDR ranges, set 0.0.0.0/0 and In Source port ranges, set *.
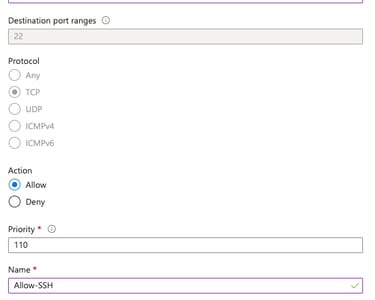
For the Destination, set Any and choose Service as SSH, destination port ranges will be automatically 22, and protocol as TCP.
Choose action as Allow.
Choose Priority as 110.
Name as Allow-SSH.
Description as you prefer.